Picking up from the last time after my two-month long hiatus, I bring you now the greatest security threats of 2008: Storm and MPack.
Storm Blows Web 2.0 Away
The Storm malware is actually a collaboration of Web 2.0 techniques like social networking and dynamical associations towards a system. Simply put, it uses the most common web techniques in a two-stage attack, which we discuss later.
According to IronPort’s 2008 Internet Security Trends, Storm-class malware has its key characteristics:
Self-Propagating – sends massive amounts of spam to spread. Users are directed to multiple changing HTTP URLs, which serve Storm malware. If infected, the system then becomes part of the network.
Peer-to-Peer – where previous botnets were controlled from centralized locations through a hierarchical management structure, nodes communicate through a unique peer-to-peer communication protocol. This makes it difficult to track the total size.
Coordinated – Storm will send spam campaigns that point to webpages hosted by other computers, showing amazing sophistication in the way the network creates its attacks.
Reusable – can be used for many kinds of attacks: spam, phishing, DDoS, it has even been known to compromise IMnetworks and post blog spam, making it a threat to many different protocols.
Self-Defending – Storm watches for signs of reverse engineering or analysis. It repeatedly launched massive denial of services attacks against researchers and anti-spam organizations.
Through these, Storm was able to accomplish a huge number of PDF, XLS, MP3 spam outbreak over the course of 2007 and even up to today.
Storm Signaling: The Two Attack Stages
Storm uses e-mail functions and interconnectivity of Web 2.0 in order for its two-stage attack to take place. Also, Storm creators have come up with a “drive-by” browser exploit that infects computer simply through a web page visit, no downloads needed for infection!
Once a Storm malware infects a computer, it connects its victim computer into a peer-to-peer network, the Storm Network. This network is a modified design, decentralized and excessive, unlike its older, centralized ancestor. The creators seemingly acknowledged the fact that a centralized network is easy to destroy just by “chopping the botnet’s head off.”
Apart from the peer-to-peer feature, Storm also needs to maintain itself via self-defense measures. It utilizes Distributed Denial of Service to both prevent people from exploring the innards of a Storm malware, and launch a retaliatory attack to the onlookers.
Once the Storm network has possession of the victim system, it can instruct its victim to do either send a recruitment spam and aid in the network growth, serve malicious web pages, attack instant messengers, provide fast-flux and domain resolutions, or post blog spams on other websites. These actions can ensure that Storm will persist even if some of its victims are paralyzed, because it launches large-scale attacks that recruit other victims into its network.
Storm doesn’t actually attack head-on, as most of its deceased ancestors did. Unlike those suicidal malware, Storm-class malware seem to value its life, that it focuses more on its staying power than its destructive one. It is very frightening to know that while the Storm hasn’t completely been eradicated, its designers are improving it at a fast pace.
MPack: The Marketed Malware
MPack is actually a malware kit that is sold for anywhere between $700 and $1, 000. It is a PHP-based malware kit being sold by a certain group of Russian software developers known as the Dream Coders Team. In a CNET interview, Yuval Ben-Itzhak, chief technical officer of security company Finjan, stated how dangerous the Mpack kit is. “Without any computer science skill or any security background, you can install this package on any Web server and start to infect people with malicious code,” said Ben-Itzhak in the interview.
The commercial malware, as I would like to call MPack, is designed specifically for web-based attack, pretty much like Storm. It is deployed using an iFrame attack placed silently into legitimate websites, keeping infection and, interestingly enough, its attack statistics. Further, its creators, the Dream Coders Team, gives one-year support, fresh exploits (like the one Storm has), and add-ons that can cost anywhere from $50 to $300,possibly based on attack modifications.
While having these kind of malicious kits in the market is not that new, support services do seem to be appealing, especially for a novice who wants instant ability over malware infection.
MPack Attacks!
MPack kit owners are provided with an administrative interface to launch their attacks, usually by the same drive-by exploits utilized by Storm. Further, the interface keeps the statistics on both viewers of an infected web page and the successful attacks it carried on. It somehow gives satisfaction to the user for purchasing the malware kit, not to mention the support services and “additional arsenal” that can make a novice a force to reckon with.
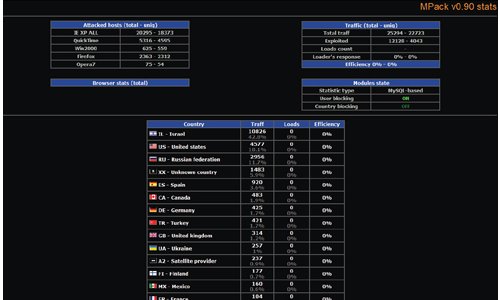
Storm and MPack malware have been spreading like wildfire since mid-2007 that it has become very alarming. The things most feared about the two are their peer-to-peer and self-defense mechanisms that allow the malware to creep into a network and destroy it from within. Also, considering that the protocol used by both Storm and MPack is HTTP, it’s really hard to recognize a social malware from a safe web page. Without a plug to pull or a switch to turn it off, it has come to attention that these malware can be considered professional in a sense – there are experts behind the longevity of these malicious software. The question that arises now would be: How can we avoid being attacked by these malware?
For Safety And Precaution
Increased sophistication. That phrase summarizes the greatest threats of 2008, although conventionally, malicious programs still do what they do best: advertise, infect, steal data, and spread. In their line of evolution, developers learned that a one-step approach is no longer plausible, and the improved two-step route they are taking is more than anyone can handle.
With a new way to launch attacks while ensuring a defensive mechanism for themselves, Storm- and MPack-like malware are hard to deal with. They easily render previous security measures obsolete. In order to protect your system from those malware, new ways are being preached and practiced. IronPort’s 2008 report summarizes these safety measures into five:
1. Secure web traffic. The reputation of a website is a key to determine how plausible a malware can infect it. Let’s have Yahoo for example. It’s reputation as legitimate and virus-free makes it hard for user-generated malware to penetrate it.
2. Deploy preventive protection for e-mail. The alarm brought about by Storm- and MPack-class malware calls for multi-level spam defenses, commonly available in our favorite e-mail service providers. Deploying these defenses can easily detect and separate possible malware attachments.
3. Protect against corporate data loss. Commonly, attacks from malware scans your hard drive to collect private information. It wouldn’t hard a company if it would require its employees to scan outgoing transfers and connections for possible policy violations. It would show how cautious your company is and give it a reputation for safety, adding to its market level.
4. Prevent “phone-home” activity. It is very important to scan or totally block outgoing “phone home” activities, as the sender might be malware-infected, retrieving attack commands or uploading data back to operators.
5. Track important communications. New technologies are available for real-time tracking of your e-mail messages, which works similar to physical package shipping. Added care wouldn’t hurt to our noble and easily accessible e-mail accounts, as they have become an integral part of our virtual lives, while others keep on attacking us through them.
Malware sure has spread everywhere on the Internet, but we should still be the masters of our own virtual spaces. I hope this four-part series will aid you through the rest of 2008! Happy surfing!