It’s no secret that nearly every home has a computer or cell phone. As people continue to increase their reliance on electronic devices like a computer, laptop, cell phone and tablet they also leave behind the places they visit on the internet, their emails, as well as their conversations. Because of this, many law enforcement agencies and attorneys are using legal discovery services to retrieve this information and use it as evidence in court cases. [Read more…] about The Vital Role of Digital Forensics in Court Cases
Search Results for: "DATA"
Tips For Picking The Right Phone Tech For Your Needs

Not everyone needs a smartphone. That’s definitely an unpopular opinion these days, but in a sense, smartphones are simply for people that want to spend time online no matter where they are at. People that are addicted to apps may not be able to survive without a fancy phone, but those that simply want a phone to keep them in contact via voice, or text, and have no intention of using social media may be able to get away with a normal old flip phone.
Here are some things to consider when it comes to picking the right phone tech for yourself. From which phone you might want to get to what accessories you are likely to want to get with it. [Read more…] about Tips For Picking The Right Phone Tech For Your Needs
Studypool Review: Micro-Tutoring Done Right
Going online to get educational help is not a new idea. However, constant innovations to the ed tech industry means that more students than ever are logging on for tutoring services. With many looking for quick and easy help as opposed to full-blown tutoring services, micro-tutoring has become a popular option. Studypool is a site that has revolutionized this learning concept. [Read more…] about Studypool Review: Micro-Tutoring Done Right
Tips For Shopping Online Safely

These days shopping online has become so convenient and popular that studies show 75% of Americans count on it as their go-to for purchasing products before going to a store. Not only is it more convenient to shop online, but in many cases, it is significantly cheaper.
With this great convenience and savings, however, also comes the risk of your private information being stolen from you. Giving out your address and payment information makes you a target for cyber criminals. [Read more…] about Tips For Shopping Online Safely
Working Loud and Proud In the Cloud

The era of the Cloud has arrived. Early adopters jumped in and have been swimming around in the misty globules above the earth for some time now. And the rest of the world is joining in, personally, professionally, and theoretically. But the Cloud really isn’t in the sky. It’s more like it’s an extension of your fingertips, and an outreach of your brain, and in reach of your computer’s processing power. Have you embraced it yet, you technological wizard, you?
If you missed the early train, you still might need a briefer on the Cloud, but after that, you can decipher where in the puzzle infrastructure, personal and business use, media consumption, and storage security fit. It’s all as fascinating as it is practical. [Read more…] about Working Loud and Proud In the Cloud
Understanding the Secure Development Life Cycle
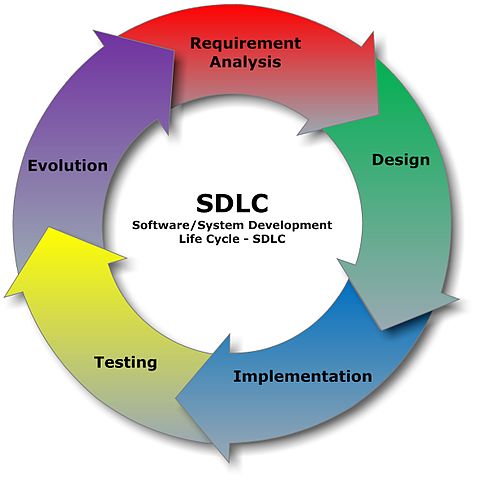
It takes research, development and testing to deploy a secure web or mobile application that users can access or download with confidence. Application security is one of the biggest concerns in the tech world today. Many people are concerned that hackers will be able to exploit unlocked doors in the virtual world to break into their computers or mobile devices. Developers and those who support apps need to stay on top of the latest trends in secure development.
An application has the best chance of staying secure if it is developed using what is known as a secure development life cycle (SDLC). SDLC is comprised of seven phases. Each phase allows developers to build the most secure and user-friendly version of an app. Planning ahead by using an established life cycle makes it easy to anticipate and repair any vulnerabilities that may come as a result of the front-end design or back-end coding of an app. This approach can help developers avoid costly and unexpected security-related discoveries in the last stages of development. [Read more…] about Understanding the Secure Development Life Cycle